INTRODUCTION
This project involves collecting and presenting network forensics information as an “expert witness” by investigating (simulated) real-world cyber-attack incidents that have affected a multi-million dollar corporation’s E-business.
In July 2001, a cyber-attack called “Code-Red” infected more than 350,000 Microsoft IIS servers and brought down several web application infrastructures. In January 2003, another cyber-attack called “Slammer” disrupted services of nearly 75,000 computers. Figures 1 and 2 show the increasing number of cyber-crime incidents that are taking place on the Internet today, which are costing billions of dollars of business-losses. For investigating such cyber-crimes affecting computers in Industry and Government networks, Network Forensic Experts are called upon!
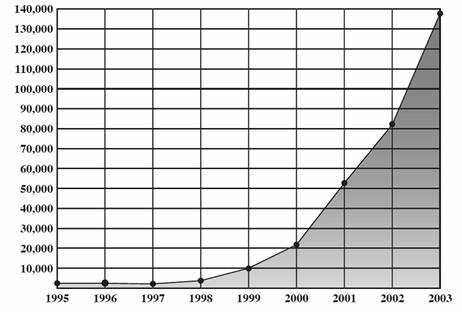
Figure 1: Number of cyber-crime incidents reported every year
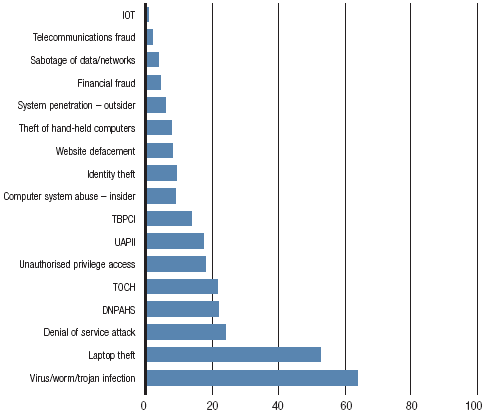
Figure 2: Cyber-crime incidents experienced in 2005 by type of incident and percentage of surveyed
organizations (survey published by the Australian High Tech Crime Centre)
A network forensic expert uses his/her vast knowledge of cyber-attacks, legally justifiable methods and a set of network traffic monitoring tools to collect evidence for legal proceedings of a cyber-crime.
THE PROJECT
You will conduct a cyber-crime investigation as a network forensic expert. For this, you will use tools such as Wireshark packet capture tool and Snort Intrusion detection/prevention tool in a “Honeynet” that has been built at OSC. A Honeynet shown in Figure 3 is a network that includes computers that need to be protected. It appears to a hacker as a real-system while infact, it carefully monitors the hacker attacks and collects clues to trace the hacker’s location on the Internet. In addition, you will use open-source software such as Mysql database and the Ploticus graphing package.
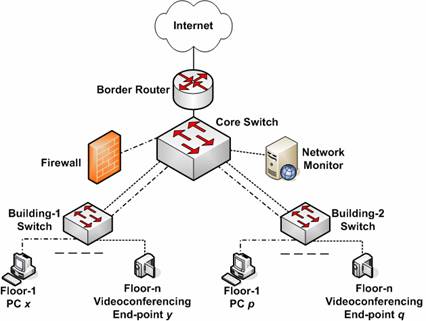
Figure 3: OSC Honeynet Setup
The general steps of the project are as follows:
- Study the setup of the OSC Honeynet,
- Monitor the Honeynet’s traffic for (randomly simulated) cyber-attacks,
- Use the Snort and Wireshark tools to analyze the collected traffic-traces/Mysql-logs and detect the cyber-attacks,
- Prepare legal evidence (text and graphs) that indicate: (i) times of occurrence and types of cyber-attacks detected, (ii) possible geographical locations of the hackers, and (iii) how these cyber-attacks could have been prevented.
ANIMATIONS
SI2012
SI2008
SI2007
Prasad Calyam is the group leader for the Network Forensics project. His office is in cubicle 450-24, phone 292-8107.
For assistance, write si-contact@osc.edu or call 614-292-0890.